Security testing is an approach that detects the security mechanisms of a system that protects their data and maintains proper functionality as intended.
Due to the logical limitations, passing security testing is not an indication that no flaws exist or that the system adequately satisfies the security requirements.
Jump to Section
Introduction to Security Testing
Security involves various elements, including confidentiality, integrity, authentication, availability, authorization, and non-repudiation. The actual security requirements that are tested depend on the security requirements implemented by the system. Security testing, as a term, has a number of different meanings and can be completed in a number of different ways.
What Is Security Testing?
Security testing is that technique or process which protects the system and application to free from any loopholes that can cause a big loss to the respective organization.
The process of security testing of any system is about finding all possible loopholes and weaknesses of the system which might result in a loss of information at the hands of the employees or outsiders of the organization.
The goal of security testing is to identify the threats to the system and measure its potential vulnerabilities. It also helps in detecting all possible security risks in the system and help developers in fixing these problems through coding.
THE IMPORTANCE OF WEB APPLICATION SECURITY TESTING
Today, millions of web applications exist to make our lives easier and much more interesting. We can shop online, pay the bills, chat with friends and relatives, or communicate with people all over the world who have the same hobbies and interests as ours. Web applications make us believe that whatever we imagine can happen on the web.
But not all of us have the same perception of those applications. The reality is that there are always “malicious” attackers trying to destroy the web “paradise” by attacking web applications and stealing data.
Some Key Terms Used in Security Testing
Now proceeding further, first, we will understand the few terms of Security Testing:
What is “Vulnerability”?
This is the weakness of the web application. The cause of such “weakness” can be due to the bugs in the application, an injection (SQL/ script code), or the presence of viruses.
What is “URL Manipulation”?
Some web applications have an additional feature to communicate between the browser and the server in the URL. Changing some information in the URL may sometimes lead to unintended behavior by the server and this termed URL Manipulation.
What is a “SQL injection”?
This is the process of inserting SQL statements through the web application user interface into some query that is then executed by the server.
What is “XSS (Cross-Site Scripting)”?
When a user inserts HTML/client-side script in the user interface of a web application, this insertion is visible to other users and it is termed as XSS.
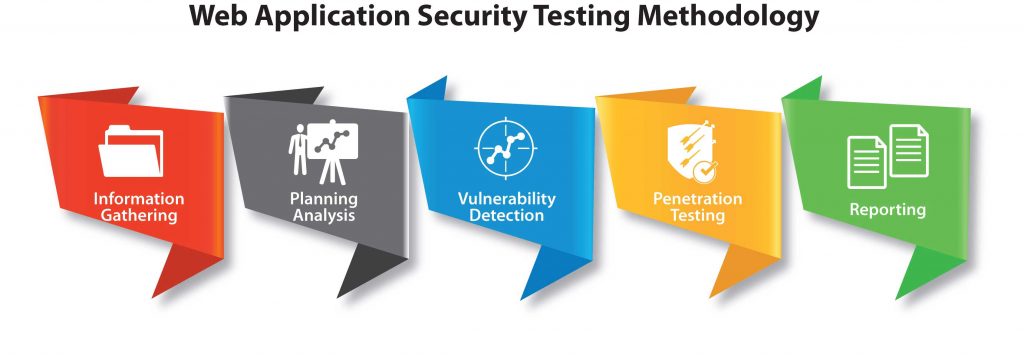
Security Testing Approach
In order to perform security testing for web applications, a tester should have a good knowledge of HTTP protocols. And moreover, it’s mandatory to have an understanding of client and server using HTTP.
Additionally, the tester should at least know the basics of SQL injection and XSS.
Hopefully, the number of security defects present in the web application will not be high. However, being capable of describing all the security defects accurately with all the required details will definitely help.
1. Password Cracking
In Web applications, security testing can be started by “password cracking”. In order to login to the application, one can either use some password cracker tool or guess a username/password. Common usernames and password lists are available along with open source password crackers.
If the web application does not enforce a complex password (E.g. with alphabets, numbers, and special characters, or with at least a required number of characters), it may not take very long to crack the username and password.
If an un-encrypted username or password is stored in cookies, it can be used by an attacker to steal the cookies and hence the information stored in the cookies like username and password.
2. URL Manipulation Through HTTP GET Methods
A tester should check whether the application passes important information in the query string or not. This happens when the application uses the HTTP GET method to pass information between the client and the server. The information is passed through the parameters in the query string. The query string can be modified by the Tester to check if the server accepts it.
Via the HTTP GET request, user information is passed to the server for authentication or fetching data. A GET request is sent to a server to get the required information or to corrupt the data. The attacker can manipulate every input variable. In such conditions, any unusual behavior by an application or web server is the doorway for the attacker to get into the backend.
3. SQL Injection
The next factor that should be checked is SQL injection. Entering a single quote (‘) in any textbox should be rejected by the application. Instead, if the tester encounters a database error, it means that the user input is inserted in some query which is then executed by an application. In such a case, the application is vulnerable to SQL injection.
SQL injection attacks are very critical as an attacker can get vital information from the server database. To check SQL injection entry points into your web application, find out the code from your codebase where direct MySQL queries are executed on the database by accepting some user inputs.
If the user input data is crafted in SQL queries to query the database, an attacker can inject SQL statements or part of the SQL statements as user inputs to extract vital information from a database.
Even if an attacker is successful to crash the application, from the SQL query error shown on a browser, the attacker can get the information they are looking for.
4. Cross-Site Scripting (XSS)
A tester should additionally check the web application for XSS (Cross-site scripting). Any HTML E.g.<HTML> or any script E.g. <SCRIPT> should not be accepted by the application. If it is, then the application can be prone to an attack by Cross-Site Scripting.
The attacker can use this method to execute a malicious script or URL on the victim’s browser. Using cross-site scripting, an attacker can use scripts like JavaScript to steal user cookies and information stored in the cookies.
Many web applications get some useful information and pass this information in some variables from different pages.
E.g.: http://www.examplesite.com/index.php?userid=123&query=xyz
The attacker can easily pass some malicious input or <script> as a ‘&query’ parameter which can explore important user/server data on the browser.
Important
The Tester should be very careful not to modify any of the following at the time of Security Testing :
- Configuration of the application or the server;
- Services running on the server;
- Existing user or customer data hosted by the application.
Additionally, a security test should be avoided in a production system.
Summary
The purpose of security testing is to suspect the vulnerabilities of the web application so that developers can
remove those suspects from the application and make the application and data safe. I hope the topic is much clearer now.
- COVID-19: How We Are Dealing With It as a Company - March 23, 2020
- Agile Testing – The Only Way to Develop Quality Software - February 8, 2019
- How to Perform System Testing Using Various Types Techniques - May 16, 2018


